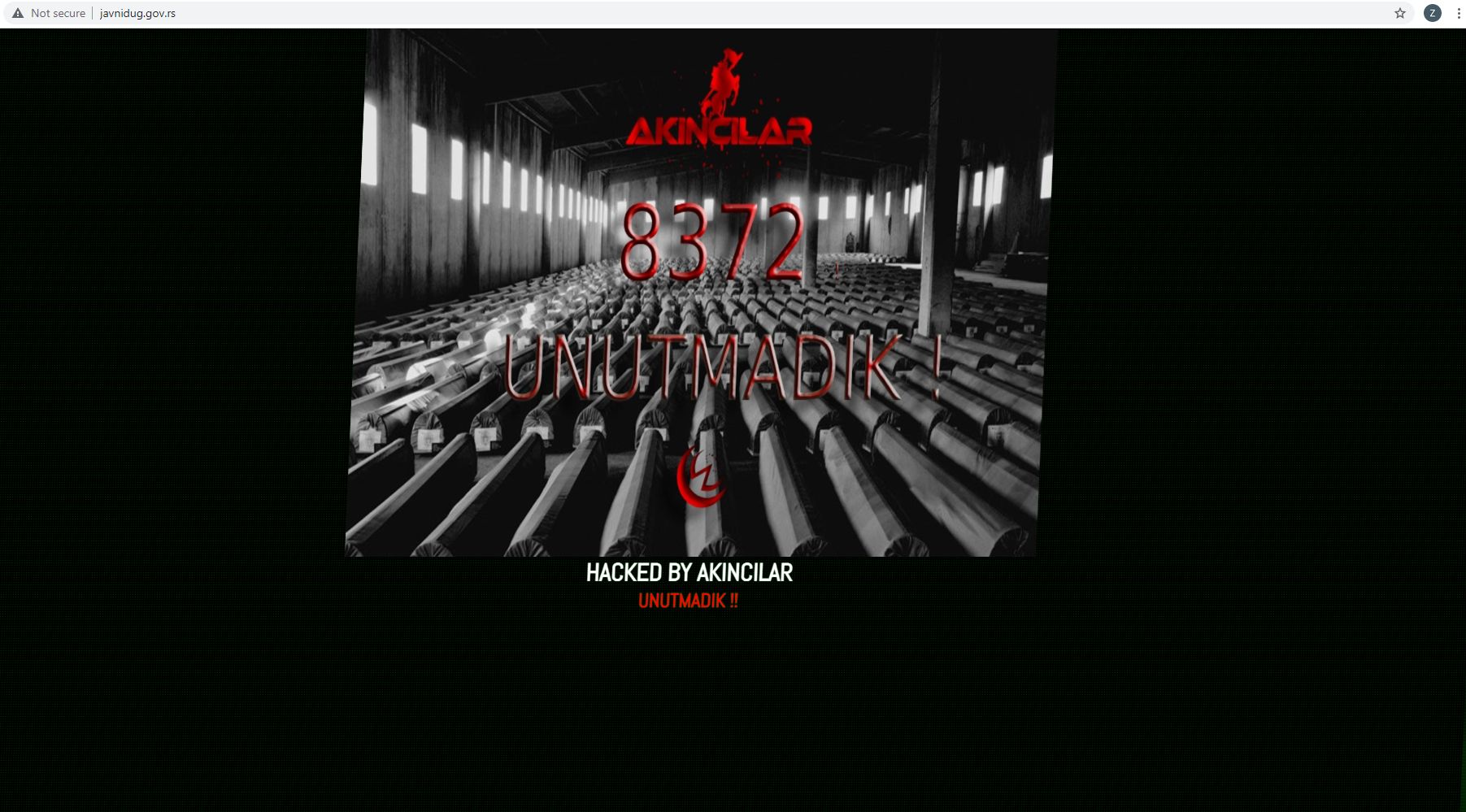
A Turkish group called Cyber Warrior Tim Akincilar hacked the Serbian Public Debt Administration’s website on Friday in what appeared to be a protest against Serbia’s denial of the Srebrenica genocide.
On the Public Debt Administration site’s front page, the hackers posted a photograph of a hall full of coffins and the number 8372 – a reference to the number of Bosniaks killed by Bosnian Serb forces in the Srebrenica genocide in July 1995, Serbian news website 021 reported.
Over the photo were the words “Unutmadik”, Turkish for “We haven’t forgotten”. This was also a reference to a quote by the first Bosnian President Alija Izetbegovic, who said: “Do not forget genocide, because a forgotten genocide will be repeated.”
The photo posted by the hackers was taken down and the Public Debt Administration site was functioning normally again on Friday afternoon.
The Serbian authorities do not accept that the massacres and deportations of Bosniaks from Srebrenica constituted genocide, despite the rulings of international courts.
Hacking group Cyber Warrior Tim Akincilar states on its website that it was founded in 2001 and fights “attacks on our faith and moral values, actions against our state and our country, and events that negatively affect society and the public conscience”.
It has often been reported that Cyber Warrior Tim Akincilar is related to Turkish nationalist groups, while ‘Akincilar’ refers to the Ottoman army’s vanguard units.
In previous years, the hackers have attacked the websites of various Greek authorities, such as Greece’s Foreign Ministry in September 2020, but also sites belonging to the Dutch government in 2018 and the sites of some government institutions in Egypt in 2019, when these countries had disagreements with Turkish government.
In 2011, they hacked the website of French satirical magazine Charlie Hebdo after it controversially published caricatures of the Prophet Muhammad.
So far, the UN tribunal in The Hague and Balkan courts have sentenced a total of 48 people to more than 700 years in prison, plus five life sentences, for Srebrenica crimes.
The most recent was former Bosnian Serb Army chief Ratko Mladic, who was jailed for life for genocide and other wartime crimes last month.